Let us talk about how NMAP can identify the version of a service operating on a port. First, let us look at what motivates us to know about service versions on a port.
Therefore, NMAP uses some probing techniques to obtain enough information to indicate which application version is running and its version.
Why check a service’s version with NMAP?
Thus, we have to verify the purpose of the verification, for example, to check the need to update services with vulnerabilities or investigate a specific service.
Also, in some cases, we have services that use the same well-known ports, which can lead to misidentification.
Additionally, the NMAP website explains that a service like Checkpoint Firewall-1 GUI can use the same port as yak Windows chat.
Therefore, in this specific case, both services use TCP port 258.
We will present more theoretical details at the end of the article.
NMAP: Checking the Version of a Service
NMAP uses the “-sV” option to scan services and versions. Alternatively, we can use “-A” to identify the version of services.
For example, we use the command below to check the versions on a host with IP 192.168.0.2. Finally, we can check the detected services and their respective versions.
nmap -sV 192.168.0.2 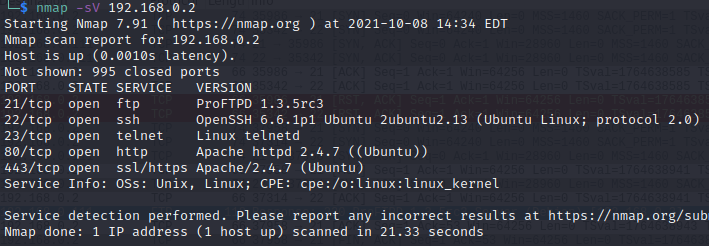
Print do wireshark
NMAP option to include all ports
—allports : This option used in conjunction with “-sV” allows us to check all ports on the host.
This way, we can check usually excluded ports such as port 9100 used by printers.
Thus, it is noteworthy that some ports, such as the 9100, can induce the printer to print pages.
Therefore, the printing pages occur because the NMAP scan sends data to the 9100 port.
nmap -sV --allports 192.168.0.2 NMAP option for scan intensity
–version-intensity 0-9 : using the -sV option, we can send a series of probes using Nmap.
Moreover, it is possible to increase the number of probes by changing the value of –version-intensity.
We can use low values in the– version-intensity if we want to send probe tests for more common services.
However, if we want to use more probe tests, we should increase the value of the–version-intensity.
However, it is noteworthy that the NMAP scan will take longer using larger –version-intensity values.
Also, it is worth remembering that the value must be between 0 and 9. In addition, the default mode uses the 7 intensity value.
However, when we target the scan to a specific port, additional tests will be performed on services operating on the port in question.
Thus, regardless of the degree of intensity, the probes for specific services of specific ports will also be tested.
nmap -sV --version-intensity 5 192.168.0.2 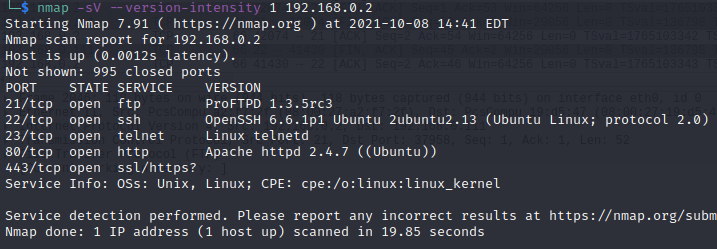
More NMAP scan options
–version-light : is the same as using –version-intensity 2 Consequently, it is a faster way to do the check, but less likely to be identified.
–version-all : is the same as using –version-intensity 9 Consequently, it is a slower way to do the check, but more likely to be identified.
–version-trace: give additional information about what the scan version is doing.
More Theory on Scanning Services and Versions in NMAP
Investigating service type and version may reveal more information about a service we collected in the “info” field.
How does NMAP show the version of a service?
This information is displayed in the VERSION column in parentheses after the name and version.
In addition, this field can include protocol numbers, such as those used in SSH, and modules, such as the Apache server.
In addition, some services may report the hostname and differ from the name provided by DNS.
Thus, the network administrator must check if the hostname information presents any risk of exposing unwanted information.
How does NMAP identify operating system?
The service identification and version-based scan can be used to speculate the host operating system.
That is because there are services that only operate on a single operating system.
Thus, NMAP can deduce the host operating system since the discovered service only operates on one operating system.
How does the NMAP database work?
The Nmap-service-probes database contains probes to check various services and matching expressions to identify and analyze responses.
This way, NMAP tries to verify the service protocol, server application name, version number, hostname, host device type, and operating system.
In addition, Nmap-service probes can get the Common Platform Enumeration (CPE) representation of the collected information.
Thus, it is possible to identify whether an X server is operational for connections and protocol versions used in SSH.
The options described allow NMAP to identify the version of the service correctly.
More about NMAP:

Juliana Mascarenhas
Data Scientist and Master in Computer Modeling by LNCC.
Computer Engineer

