Let us introduce the NMAP mapping tool. Widely used to check machines on the network and their services using port mapping on TCP and UDP ports.
Furthermore, NMAP is a handy tool in Pentest and problem investigations within a network.
In this article we present some concepts about the NMAP tool and applications in detecting nad mapping TCP and UDP port.
NMAP Installation
Regarding the NMAP installation, this can be done by downloading from the NMAP website or by package managers.
There are versions available for Linux, Windows, MAC, and others. If we choose to use it on Linux, we can use the command below for installation:
sudo apt-get install nmap NMAP first steps
For this tutorial we will use nmap which is already installed. Thus, to check the options available in the nmap tool, we can use the command below:
nmap 
Mapping Network Machines with NMAP
Now, let us start mapping the network. This way, we will use NMAP to search the machines on the network and check the available services.
Furthermore, it is noteworthy that Nmap can search for services that operate on UDP and TCP ports.
For example, let us use the command below to search for hosts on the 192.168.0.0/24 network.
nmap 192.168.0.0/24 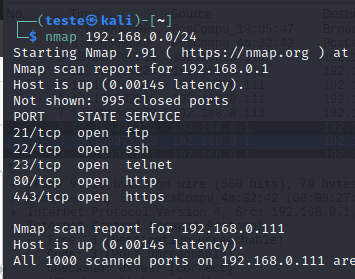
Analyzing NMAP in Wireshark
We will also investigate how Nmap discovers machines on the network. For that, let us use Wireshark.
Wireshark makes it possible to investigate packets collected from the network or a specific host. Other features are available in Wireshark, but we will discuss that later.
NMAP discovering open TCP ports
The first way that Nmap uses to discover open TCP ports uses SYN packets. Therefore, SYN NMAP sends an SYN packet and waits for an SYN+ACK response.
Then, NMAP sends an ACK packet to complete the transaction. This default Nmap scanning uses the 3-way connection from TCP.
The NMAP interprets that the port is open when it sends an SYN and gets a response(SYN+ACK) that continues the connection. However, when it receives an RST, Nmap interprets that the port is closed.
The RST response occurs because, in typical environments, a host responds with RST to requests to closed ports.
Does
Does NMAP always respond to SYN packets?
No, because we may have equipment or software filtering responses from a particular host. Therefore, the host can drop the connection request instead of responding with an RST. In that case, the port might appear as filtered.
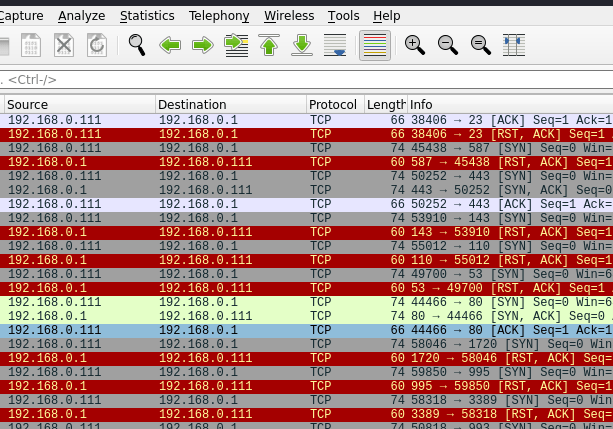
We will use WIreshark to investigate NMAP-related behaviors in TCP and UDP port mapping.
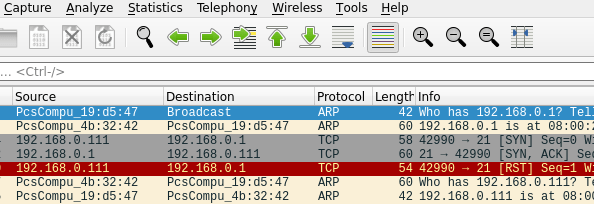
Looking at SYN, SYN+ACK and RST packets
We can observe in Wireshark packets SYN, SYN+ACK, ACK, and RST. Here we can see the NMAP behavior when checking the services that run on the investigated ports.
nmap Scan with the -sT option
This option follows the default nmap scan, running TCP 3-way to detect if a port is open.
nmap -sT 192.168.0.1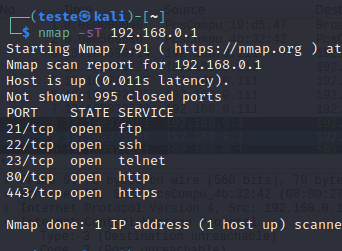
NMAP: scan with -sS option
Another way to scan TCP ports is with the “-sS” option. In this option, Nmap sends a SYN and waits for a SYN+ACK. Then, Nmap closes the connection and sends an RST to the target.
Therefore, Nmap does not complete the 3-way TCP connection. Thus, using “-sS” we can do port scan faster and quieter than the “-sT” option.
sudo nmap -sS 192.168.0.1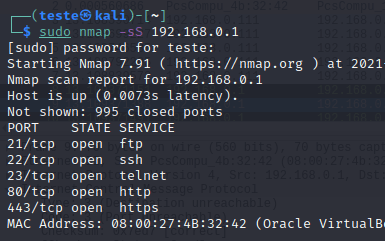
NMAP: Scan an specific port -p
Nmap also allows us to specify the port that we want to probe. To do this, we use the “-p” option and the port we want to check. This option is attractive when we want to check a specific service on a host.
For example, we will scan port 21, which belongs to the FTP protocol.
sudo nmap -sS 192.168.0.1 -p 21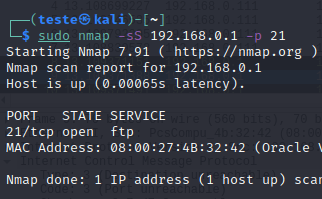
How NMAP Scan a list of ports ?
Another exciting option is to specify a list of ports, for example, from ports 20 to 30. For this, NMAP use the option -p followed by the first port and “-” followed by the last port.
sudo nmap -sS 192.168.0.1 -p 21-23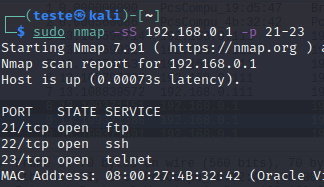
Fast NMAP Option
We can use the “-F” option for faster port scanning. This “-F” option checks the 100 commonly used ports instead of the 1000 ports used in the standard Nmap scan.
sudo nmap -F 192.168.0.1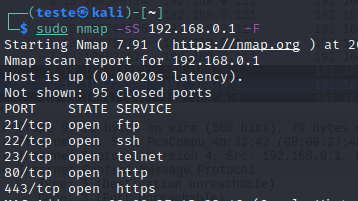
nmap Scan UDP ports –sU
Nmap also scans UDP ports. For that, Nmap sends packets to the host’s UDP ports and waits for an ICMP destination unreached message.
sudo nmap -sU 192.168.0.1How do I know if a UDP port is open?
Nmap will assume that a port is open or filtered when there is no ICMP response indicating that this port was unreachable.
Therefore, NMAP assumes that a port is open or filtered because an open port will not return any response which suggests it is open. However, the target host or a firewall can filter ICMP responses. Therefore, Nmap cannot be sure if the port is open or filtered.
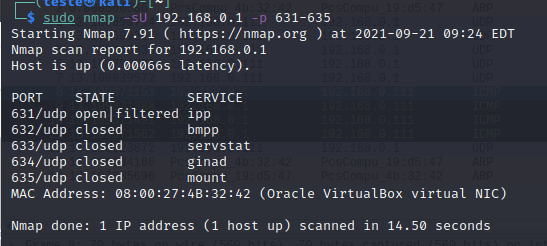
Why does nmap scanning UDP ports take time?
Scanning UDP ports can take a long time. This delay occurs because some operational systems, such as Linux from kernel 2.4.20, limit the sending of ICMP destination unreachable by 1 per second.
Thus, this makes scanning 65,536 ports take over 18 hours. However, there are techniques to scan popular ports and multiple hosts in parallel, which we can discuss at another time.
UDP Scan Analysis in Wireshark
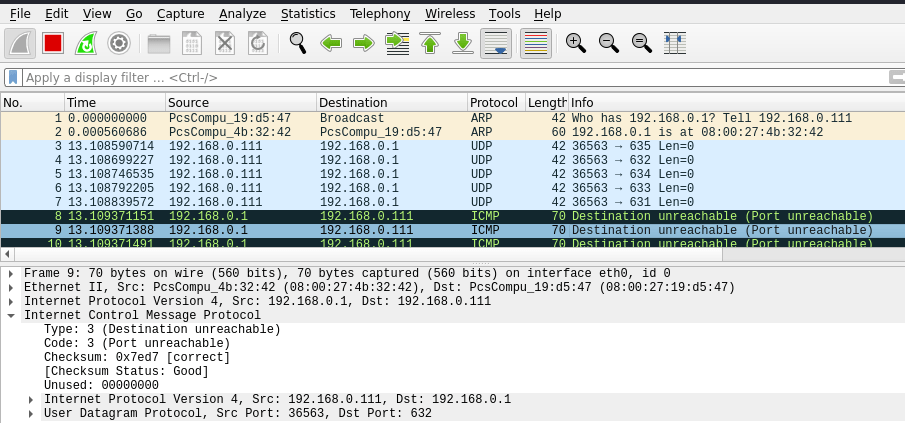
Why does the nmap UDP scan repeat the udp packet?
Every UDP packet can be lost, and the ICMP reply showing that the port is unreachable can also be lost. In this way, Nmap repeats the sending of UDP packets to ensure that there have been no losses.
You have completed the first class on NMAP TCP and UDP Port Mapping
Comment if you would like to see more posts about NMAP. There are several possibilities to use NMAP for TCP and UDP port mapping.
See More:

Juliana Mascarenhas
Data Scientist and Master in Computer Modeling by LNCC.
Computer Engineer

