How does a Blockchain work? We present in this article in general the functioning of a platform based on Blockchain. When there are broad issues that need to be mentioned, a brief explanation will be given. These topics will be in other articles. If there are already related articles, they are available through the links provided throughout the article.
Byzantine Consensus
The blockchain is based on fundamental concepts of distributed computing. As such, one of the pillars of technology is fixed on the problem of Byzantine generals that defines the Byzantine consensus. In computing, consensus allows several participants in the network to coordinate their actions while maintaining a consistent state. In this case, all participants must have the same information for consistency.
A consistent network remains operational even with failures. Failures may still be malicious processes trying to modify the information, yet the network must be able to reach consensus. However, who maintains the consistency of a network? The maintenance of the state, the information that composes it, as well as the mediation between the participants is traditionally carried out by a trusted entity. The trusted third party, enables this scenario within a permitted network. In Blockchain this work is performed by consensus protocols.
Electronic Logbook – Ledger
We can view the Blockchain as a distributed electronic logbook. This book is replicated on every node belonging to the network. Every event that takes place within the network must be “written” in this book. The consistency of this record is carried out by the consensus mechanism adopted by the platform. There are private, hybrid and public Blockchains. In order to maintain a general explanation, we take the public as a reference.
This ledger is similar to a registry office. The record on the ledger is public, that is, all information can be read and verified by its users. Blockchain is a technology composed of several computing techniques that provide a reliable distributed computing. Another way of looking at it is as the implementation of a replicated state machine.
The idea of a structure similar to a Blockchain existed before Nakamoto. However, with the problem of the Byzantine generals. Nakamoto introduced an idea of consensus protocols by determining Proof of Work as a mechanism for validating information within the network. PoW basically consists of a race between validator nodes in order to find an answer to a puzzle, the hash, compatible with a set of information called a block.
Later in this article, we’ll talk about how they are structured as information within the Blockchain. In summary, the consensus mechanism defines the guidelines for the validation process of the information that will be added to the Blockchain.
Blockchain Transactions
So how is the information stored and verified on the network? In traditional networks, information is verified by a trusted entity. Unlike these networks, on Blockchain information is stored in a public ledger. This ledger is distributed and replicated across all (or nearly all) nodes on the network. This information is stored in transactions with origin and destination identifier. In addition, there are other information that depend on the platform.
The transaction corresponds to a digitally signed instruction propagated within the system. These transactions are grouped together to form an organized structure called a block. Before we talk about blocks, you might be asking yourself: and what is the guarantee of the transaction veracity ? Transaction authentication is guaranteed by an asymmetric key. This subject will be covered in another article on the site. Figure 1 summarizes the process between creating a transaction and entering it into the Blockchain.
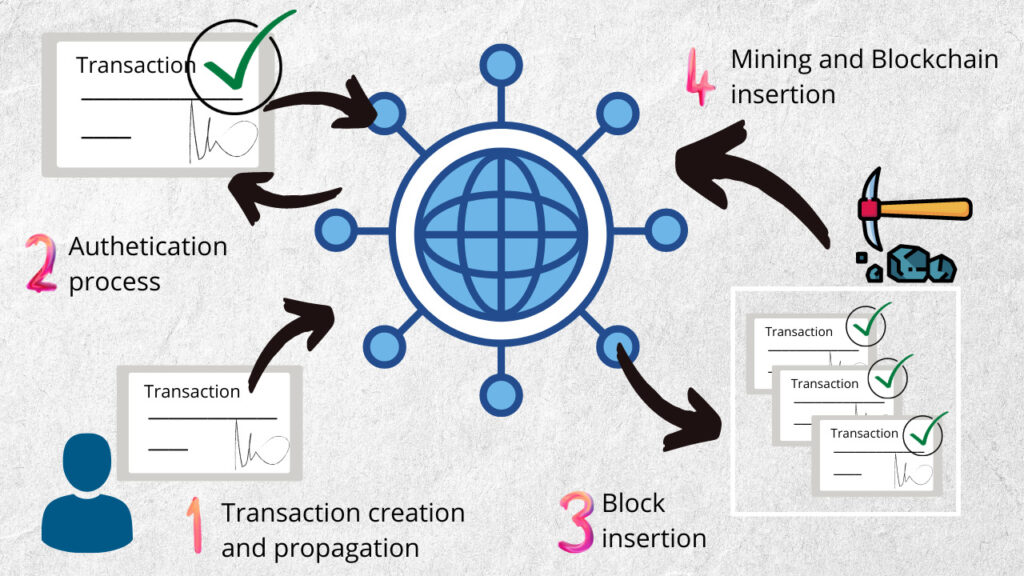
Transaction Authentication
In Blockchain an asymmetric key cryptography uses at least two keys: private and public. There is also a combination of more than one private key for signing as transactions, thus increasing the security level. However, for example, let’s consider the standard case.
When creating a transaction for an account on the system, the user will sign with his private key to later propagate it on the network. This digital signature is based on the user’s private key. Only he is able to generate this signature. Therefore, it is extremely important that the key is kept secret to preserve the authenticity of the user.
This user’s public key is associated with the private key and is used for authenticity checks. In cases of attempts to forge the authenticity of a transaction, the result of this verification process is false. Consequently, the verification process failed, characterizing a malicious process. However, applying the public key to a legitimate signature of a transaction performed by the same user returns true as a result.
Blocks – transactions grouping
After the authenticity verification process, transactions are added to blocks, as mentioned before. In addition to transactions, blocks have control fields common to several different platforms. However, these blocks are not restricted to those mentioned in this text. The main information that compose the blocks are:
identifier (hash) – result of the validation process of this block;
merkle tree – a data structure that keeps transactions organized within the block;
timestamp – time when block validation occurred;
and block reward – sum of the rewards of each transaction + block reward.
These are just some of the fields that make up a block. In Figure 2 we exemplify the possible structure for transactions on Blockchain platforms that composes the block.
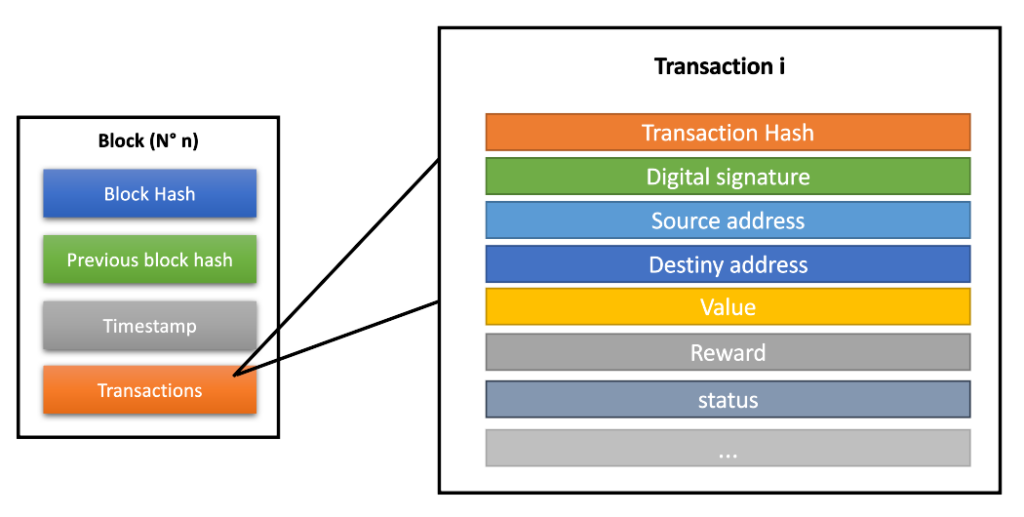
Blockchain Information Validation
After the creation of a block, it will be submitted to a validation process. Mining nodes performed computational work according to the rules of the consensus protocol used by the platform. The objective of this work is to find a unique hash (identifier) for this block.
Bitcoin uses the proof of work (PoW) consensus mechanism, while Ethereum uses the proof of stake (PoS) consensus mechanism. Once the block is validated, it is propagated through the network in order to be added to the main chain of blocks. The main chain of blocks is the Blockchain.
However, for this block to be added to the Blockchain most of the network must accept this block as part of the blockchain. For this reason there are blocks that are successfully mined but are not accepted by the network. In this case, the miner does not receive the right reward for that block. This case will be presented in another article on the site.
Chain of blocks
Before Bitcoin, Blockchain did not have any kind of verification and reliability of information. Any transaction could be added or modified without the sending user’s consent. Okay, the validated block is inserted into the chain of blocks. But how sure is it that it won’t be modified?
In this chain of blocks, each block has a pointer referencing the hash of its predecessor block. Thus, we have a linked list of blocks (as shown in Figure 3) from the genesis block (first) to the last mined block in the chain. Each block identifier, that is, the hash is the result of a hash function that has the block information as input to the function. The information that comprises this input are, the transactions (as well as all its fields), block number, timestamp, the other fields of the block and the hash of the previous block.
Each block has its hash linked to the block that precedes it. Thus, to modify information of a block belonging to the blockchain, it will be necessary to modify its predecessors. Since a information modification of the original block results in a modification of the associated hash. This happens for the other blocks that succeed it. In this scenario there is the 51% attack. If 51% of the network becomes malicious, history could be rewritten, and the Blockchain would be modified.
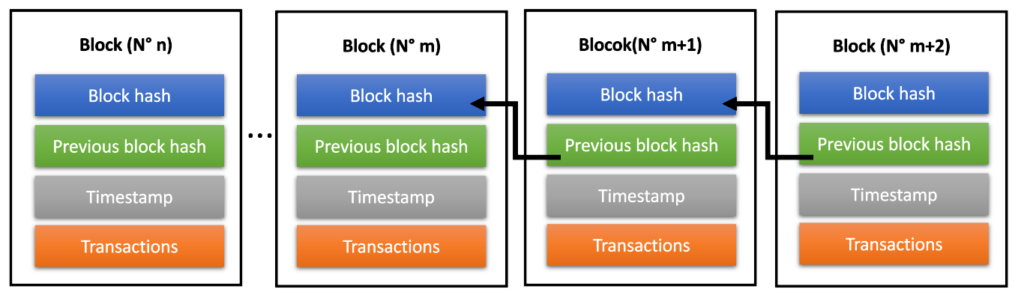
Safety Margin
Blockchain security is tied precisely to this chained list of blocks, but not restricted to it. The older a block, the more secure it is. Consequently, any type of block modification becomes more difficult or improbable. Following this logic, the more recent a block, the less certain it is that it will remain in the chain.
For this, there is a waiting time for the last block to become “safe”. Let’s reflect on the following concept… with each block added to the chain, most difficult becomes modify it. This is because the computational work that must be performed for this task becomes unfeasible. Thus, for the last block to become secure, it is necessary to “wait” for more blocks to be add on the chain.
We quote an example to clarify the point: for a certain user to be sure that his transaction (belonging to the block in question) actually happens, he must wait for the blocks to be inserted after his operation. Thus, both the sender and the user can consider that a transaction has succeed.
In Bitcoin this time is linked to 6 blocks added to the ledger. This means that the computational work time required to guarantee the transaction insertion in the Blockchain is equivalent to 6 blocks. In this way, the entire network recognizes that that transaction has taken place.
This issue, mentioned above, is linked to a bifurcation that can occur when the nodes are “listening” to the blocks in the network. The result is sometimes two concomitant lists. For this case, there is a guideline to be followed. The result is a choice from one of the lists. This topic will be addressed in another article on the site in the future.
Blockchain properties
According to some authors, Blockchain is a public distributed database where all events are shared and viewed by everyone on the network. The properties that evidence Blockchain’s qualities as an innovative technology are listed below:
- Immutability: the information entered cannot be modified;
- Irrefutability: a transaction cannot be denied;
- Availability: the network nodes reach a consensus even with the presence of node failures
- Integrity: network participants incorporate consistent and known information;
- Transparency: all events and information are transparent;
- Visibility: the authenticity of a transaction can be verified;
- Disintermediation: there is no action of a centralizing entity;
- Pseudo-anonymity: A real user ID is not known by other nodes on the network.
Since its inception, a reliable implementation of Nakamoto, a blockchain has gone through phases. These phases, according to (GREVE, F. et al.), are consolidated in 3 stages:
(1) blockchain as a state machine simplified with Bitcoin in 2008; (2) a wider range of operations is possible with the use of smart contracts with Ethereum in 2015, enhancing the use of Blockchain; (3) there is the diffusion of the use of the Blockchain in several areas such as IoT, health and government administration.
GREVE, F. et al.
This P2P network with distributed database reinvented a way to carry out transactions and agreements of different natures. From transferring values, products, or tracking information. Certainly still improvements to be made, but in the world of technology always will be. More information about Blockchain’s mode of operation can be accessed in the related articles on this website.
What is the Blockchain?
In this article from the website simplifying networks we describe the technology in a simplified way, giving an overview. We want laypeople and professionals in the profession to agree to understand what a Blockchain is and where it can be applied. Click here to be redirected to the above article page.
Main Bibliographical References
Juliana Zanelatto Gavião Mascarenhas, Artur Ziviani, Klaus Wehmuth, Alex Borges Vieira, On the transaction dynamics of the Ethereum-based cryptocurrency, Journal of Complex Networks, Volume 8, Issue 4, August 2020, cnaa042, https://doi.org/10.1093/comnet/cnaa042
Mascarenhas, Juliana Zanelatto Gavião. Modelagem e Análise Temporal da Rede de Transações de uma Plataforma de Consenso Distribuído. 2019. 123 p. Dissertação (Mestrado em Modelagem Computacional) – Laboratório Nacional de Computação Científica, Petrópolis, 2019. https://tede.lncc.br/handle/tede/299
MASCARENHAS, Juliana ZG; VIEIRA, Alex B.; ZIVIANI, Artur. Análise da rede de transações do ethereum. In: Anais do I Workshop em Blockchain: Teoria, Tecnologias e Aplicações. SBC, 2018. https://sol.sbc.org.br/index.php/wblockchain/article/view/2352
GREVE, F. et al. Blockchain e a revolução do consenso sob demanda. Minicursos do Simpósio Brasileiro de Redes de Computadores e Sistemas Distribuídos (Minicursos_SBRC), v. 36, 2018.


