Let us talk about using advanced scans in NMAP. The idea here is to present different scans from the default ones presented in the post: NMAP: TCP and UDP port mapping.
This way, we will present ways of scanning that can identify services using an unorthodox approach.
If this is your first time on Nmap, we suggest you return to the previous post concerning nmap.
This article presents:
TCP NULL Scan
The first type of scan we will look at is TCP NULL. In this scanning mode, we will use a null TCP flag header.
Therefore, NMAP sets the field which refers to the flags to zero. For that, we will use the “-sN” option. See the command below.
sudo nmap -sN -p 80 192.168.0.1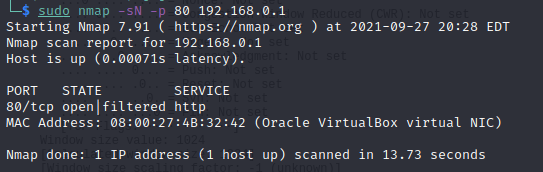
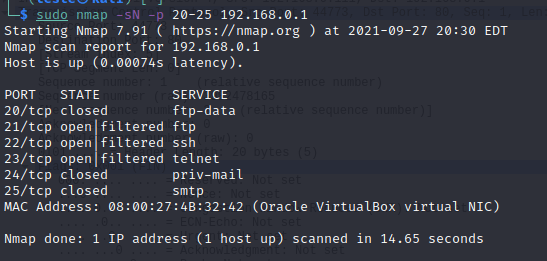
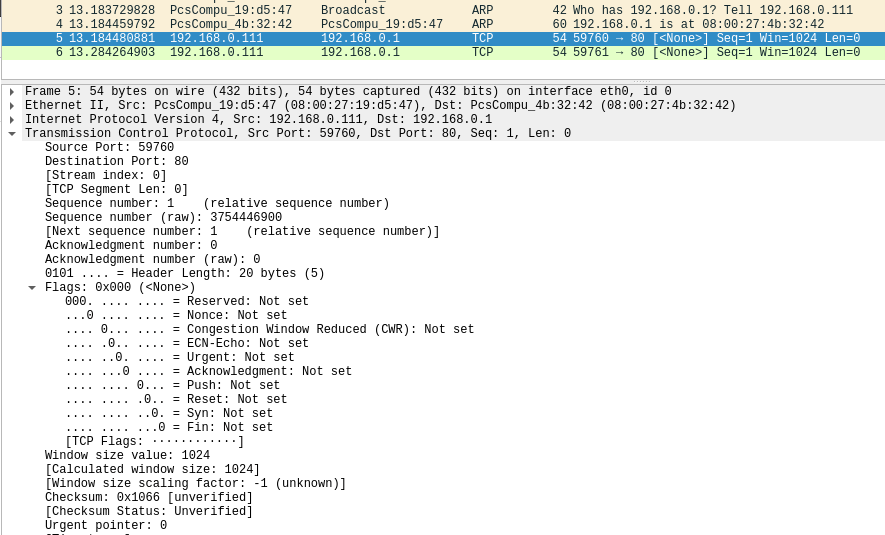
We can see in Wireshark that the TCP segments flag field sent to the target is null.
Additionally, in this type of scan, the target’s lack of response Indicates that the port is open or filtered by a firewall.
Scan TCP FIN
This scan sends TCP segments with the FIN flag. Thus, when receiving a FIN flag for a port that is not open, the system responds with a RST.
Thus, if a target does not respond to a specific port, it will be considered open or filtered.
At first, Nmap has no way of knowing if the port is open or if there is some security mechanism preventing the response.
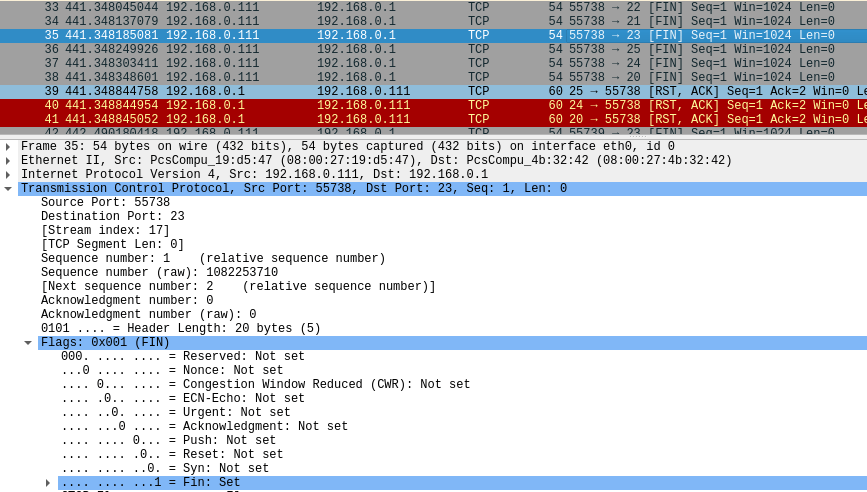
The command below uses the -sF option to indicate that a segment with the FIN flag should be sent.
sudo -sF -p 20-25 192.168.0.1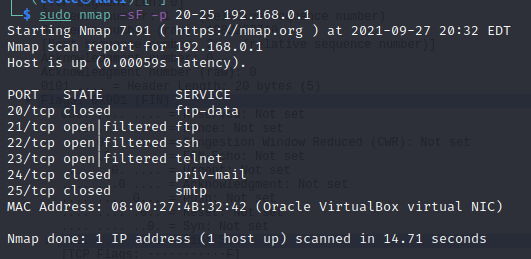
TCP ACK Scan
We now present a different scan in terms of its functioning and its purpose. First, let us talk about the objective of our scan, which is to get information if the firewall is stateful.
That way, we do not want to know whether the doors are open. Instead, we want to check if there is an RST response to our query.
If the target responds with RST, we assume we do not have a stateful firewall rule before the analyzed service.
Therefore, this scan is helpful to verify if we have correctly configured the firewall.
Example of a scan using ACK to a host at address 192.168.0.1 and ports 20 to 25:
sudo nmap -sA -p 20-25 192.168.0.1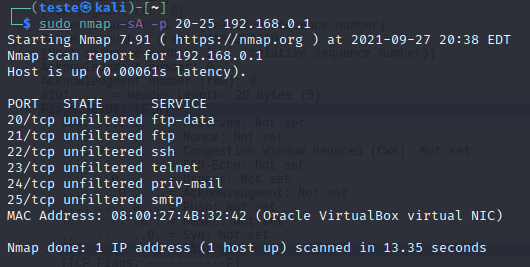
We can see that the answer was that the ports were not filtered. Thus, we can deduce that we do not have a stateful firewall between source and destination.
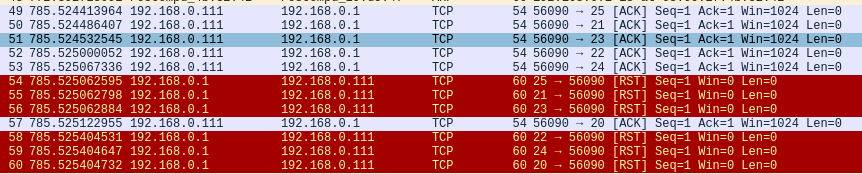
In addition, we can check the TCP segments with ACK in the Wireshark and the corresponding responses with RST.
Therefore, this result proves the thesis that the system is responding to ACK indiscriminately.
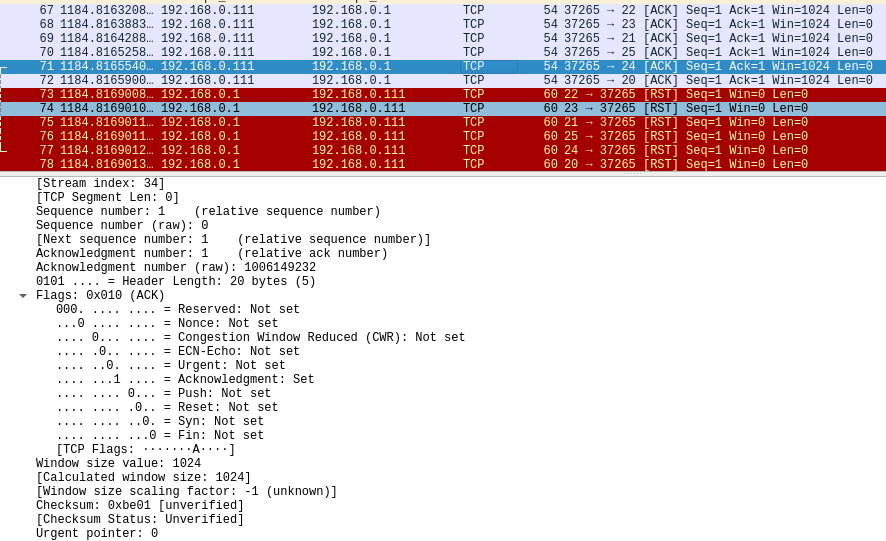
TCP Window Scan
Now let us look at a scan similar to TCP ACK that checks if the RST response uses a positive window size. This behavior is expected on some systems and can be used to check if a port is open.
Thus, in some systems, we have an RST with a positive window size, while for closed ports, we have an RST with a size 0. Therefore, it is an unusual way to obtain information about services using an advanced Scan in NMAP.
Example of a scan using TCP WINDOW for a host at address 192.168.0.1 and ports 20 to 25:
sudo nmap -sW -p 20-25 192.168.0.1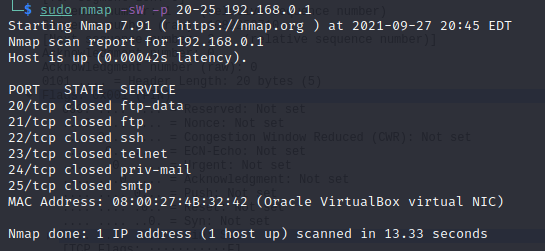
Advanced NMAP Scan with multiple flags
Another scanning option is to send a TCP segment with all flags set or a combination of more than one flag. In this way, we can verify how the target system will respond to this type of segment.
It is noteworthy that it does not matter the order in which we insert the flags in the command. This behavior occurs because the command only marks which flags we will use in the TCP segment.
Example of a scan using multiple TCP flags for a host at address 192.168.0.1 and ports 20 to 25:
sudo nmap -scanflags URGACKPSHRSTSYNFIN -p 20-25 192.168.0.1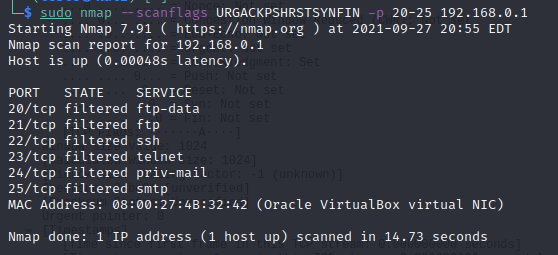

Juliana Mascarenhas
Data Scientist and Master in Computer Modeling by LNCC.
Computer Engineer

