Let’s create a list of IPs that should freely pass through the network, without any traffic restriction by PfBlockerNG. We present a way to create an exception list for clients within a network. PfBlockerNG: Creating Exception List for Clients
That way, we can have part of our users pass through the PfBlockerNG filter, while the other part of users can browse without restrictions.
PfBlockerNG Setup Tutorial:
Part 01: pfBlockerNG Customize Blocklist
Part 02: PfBlockerNG: Exception List for Clients
This type of configuration can be interesting when we have a hierarchy of traffic within the company. Therefore, in order to comply with hierarchical procedures, it may be necessary to create an exception for some specific customers.
Describing the configuration
In this configuration we make the exception of clients based on their IP address. So, based on the client’s IP, it can have its traffic restricted by the PfBlockerNG.
Consequently, to meet this traffic restriction exception, we created rules in the firewall. So, these firewall rules allow traffic to pass through before reaching the PfBlockerNG rules.
Let’s start the setup. In this scenario we are going to create a list of IPs that must freely pass through the network, without any traffic restriction.
To create this list, we will use the Aliases feature. This feature is present in pfSense in the Firewall tab.
Starting configuration for client exception list
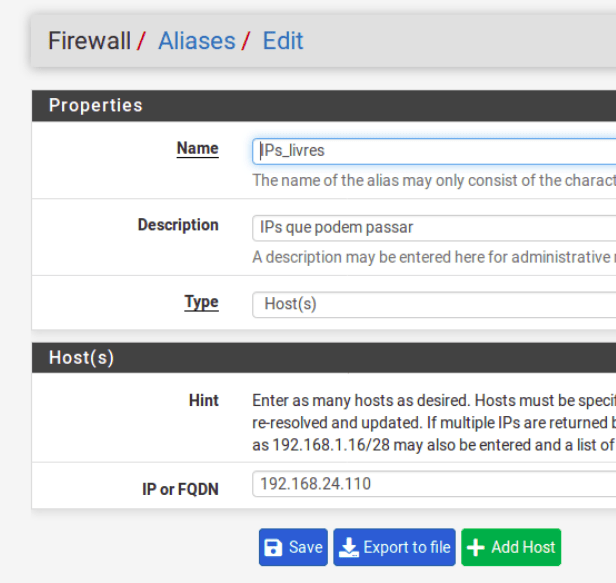
We create an alias ( Aliases) Firewall->Aliases->EDIT . Then enter the IP or IPs that should pass freely. In this case, we created an Aliases, to facilitate the insertion and removal of IPs that should have access without the pfblocker filter.
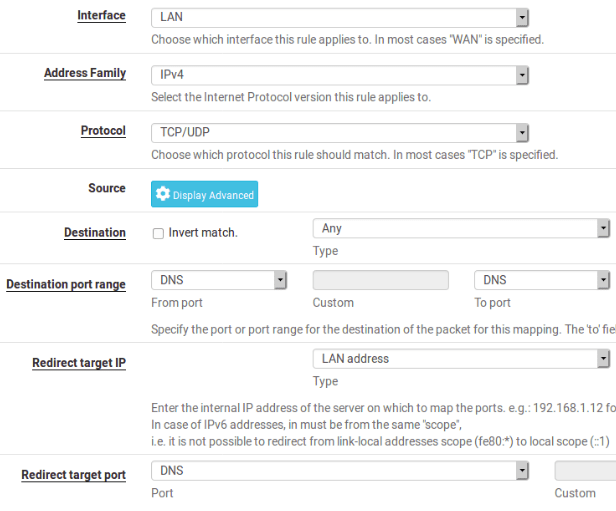
Next, let’s add rules in Firewall -> NAT -> Port Forward . Let’s create two rules, one will forward any DNS request to pfSense’s LAN interface.
The other rule will make the IPs present in the exception list, created in FIrewall->Aliases, to have their DNS requests forwarded to another DNS server.
General redirection rule
Rule for the IPs that should be filtered by PFBlocker. In this rule, we are guaranteeing that even if a client tries to use an alternative DNS it will be redirected to the pfBlocker.
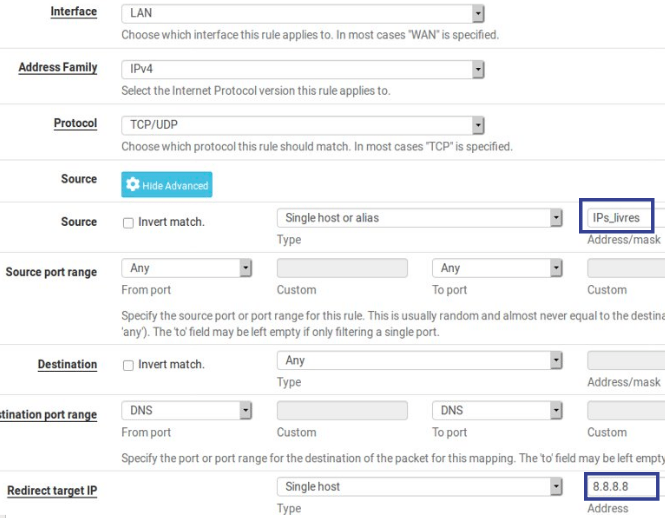
IPs that must pass freely
Rule for IPs that must pass freely. In this rule we are saying that if the origin is the Aliases (IP_livres ) the DNS query will be redirected to the DNS IP 8.8.8.8. We use 8.8.8.8, but it could be any other DNS.
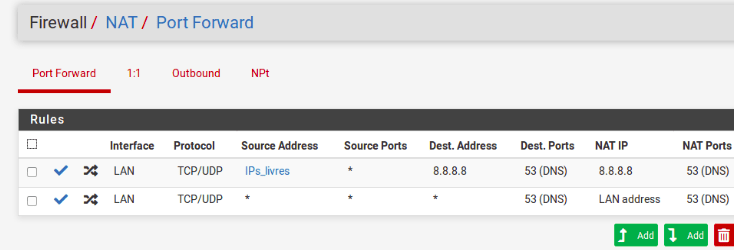
Order in which rules should appear in ( Firewall -> NAT -> Port Foward):
pfBlockerNG Customize Blocklist
PfBlockerNG Setup Tutorial:
Part 01: pfBlockerNG Customize Blocklist


