This tutorial demonstrates in a practical way how to revoke a user’s certificate on the OpenVPN server.
It is very common, when we are dealing with corporate VPNs, for employees to leave the company and therefore should no longer have access to the VPN. Furthermore, a user may have forgotten their password or even have their private key exposed.
Therefore, it becomes a basic need in a company’s day-to-day life to know how to revoke a certificate correctly and precisely.
In this tutorial, we are using an OpenVPN server that is installed on a Linux machine. Additionally, as a proof of concept, we will use an OpenVPN client with an Alice user.
Also, we are using the same scenario that we used in the article:
Revoking certificate in OpenVPN
The first step to revoke a certificate is to enter the directory containing the easyrsa file. In our previous installation of OpenVPN Server, the easyrsa file is in the easy-rsa directory. Therefore, to access it we will use the command below.
cd ~/easy-rsa/ 
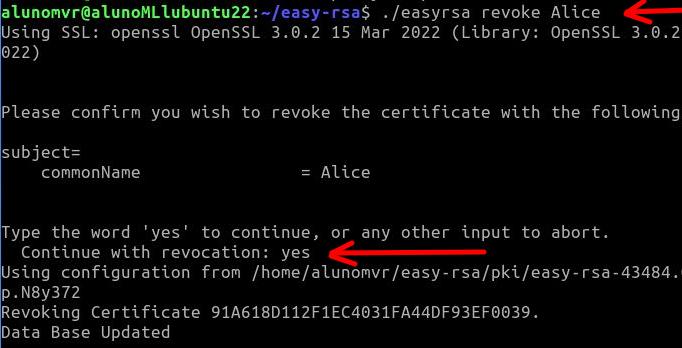
After that, we will use the easyrsa revoke command to revoke the Alice user certificate. To do this we will use the command below.
./easyrsa revoke Alice The system will ask if you want to continue and we will type yes and then press ENTER.
Generating the CRL (certificate revocation list)
Now let’s generate a CRL (certificate revocation list) for the revocation of Alice’s certificate to take effect. When using the command “./easyrsa gen-crl“ A certificate revocation list file called “crl.pem”.
./easyrsa gen-crl 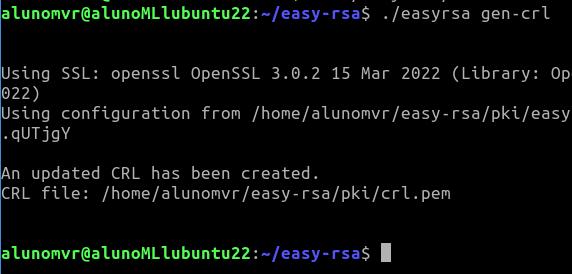
We can see that the file “crl.pem” was created inside the directory “~/easy-rsa/pki/”. If we want to check, we can use the command below to enter the directory and then use the command “ls”to list the contents of the directory.
So, we will see that we now have the certificate revocation list file called “crl.pem”.
cd ~/easy-rsa/pki/ ls 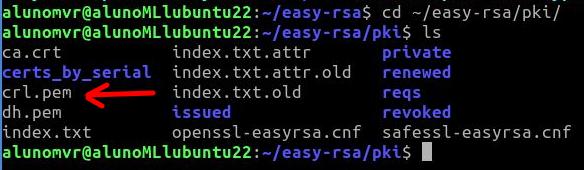
Copying the CRL (certificate revocation list) file
Now let’s copy the CRL ( certificate revocation list) file “crl.pem” to the openvpn configuration directory. To do this, we will use the command below.
sudo cp crl.pem /etc/openvpn/server/ 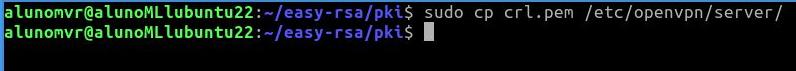
Editing the OpenVPN configuration file
Now, let’s edit the OpenVPN server configuration file to identify the CRL (certificate revocation list) file. To do this, we will use the command below to edit the file “/etc/openvpn/server/server.conf” using the nano text editor.
sudo nano /etc/openvpn/server/server.conf 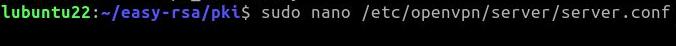
At the end of the “server.conf” file, we will insert a line that indicates the CRL (certificate revocation list) check. Therefore, we must copy the instruction below and paste it at the end of the “server.conf” configuration file.
crl-verify crl.pem 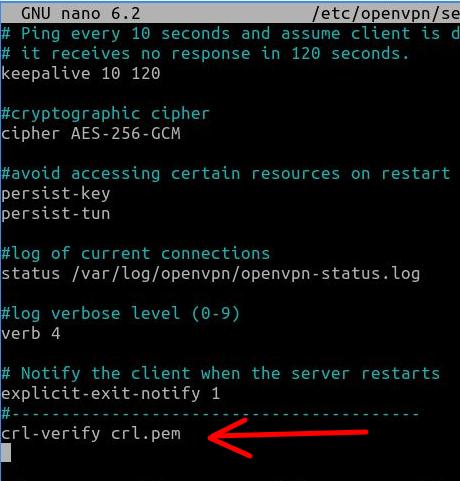
Restarting the OpenVPN server
Now let’s restart the OpenVPN server for the changes to take effect.
To do this, we will use the command below.
sudo systemctl restart openvpn-server@server.service 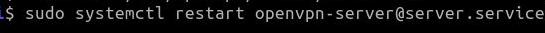
Testing revoked OpenVPN certificate
Now let’s test whether the user can still use the revoked OpenVPN certificate. To do this, let’s go to the client machine and try to connect to the VPN with the user Alice.
In our case, as we are using a Linux machine as a client, we will use the command below to connect the user to the VPN.
sudo openvpn --config Alice.ovpn 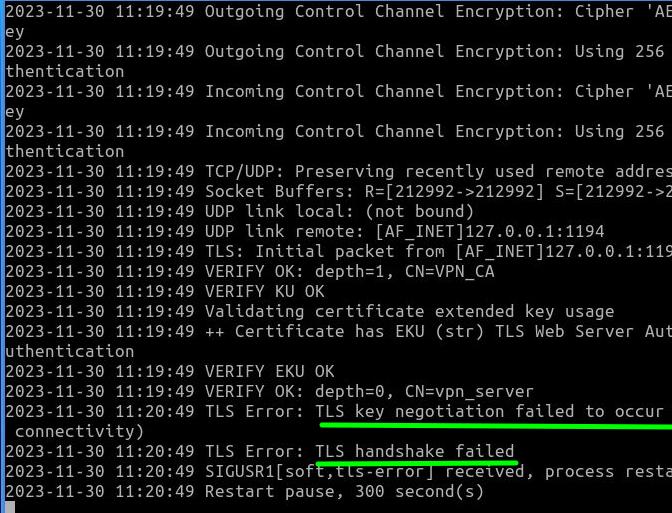
We can see that the user Alice was unable to connect to the VPN and, in addition, errors appeared such as “TLS key negotiation failed to occur” and also “TLS handshake failed”. Consequently, we can see that after revoking user Alice’s certificate, this user is no longer able to enter the VPN.
My opinion on VPNs and automation
I really like automating the certificate revocation process. This is because on a daily basis we must always try to simplify the lives of those responsible for adding new users to the VPN and removing them.
I once remember being at a computer company that produced software for devices built into TVs. On a Friday afternoon, we were informed that there would be a merger of the company with another company that until now was a competitor.
Our team was in charge of migrating the user base so that on Monday the impacts on work were reduced. In this case, we had a challenge: how to update the access of users from the original company and also add users from the company that was merging with ours.
Initially, we tried to revoke certificates and create users in OpenVPN manually. However, we quickly realized that this process could take longer than we were allotted. It was then that a colleague came up with the idea of creating a shell script to revoke all the VPN certificates that needed to be updated and within the same script create new certificates for the large list of employees that had been handed over to us.
So, we decided to follow our colleague’s idea and spent some time creating the script and validating it. And to our surprise, the script was ready faster than expected and we were able to add users to the VPN and revoke certificates quickly, reducing the likelihood of human error. This way, work that was supposed to be delivered in 3 days was done in just one Saturday morning.
This was just one episode of my life working with information technology, I hope it helps.

Juliana Mascarenhas
Data Scientist and Master in Computer Modeling by LNCC.
Computer Engineer
Congestion Control in Networks: Optimizing Efficiency and Bandwidth Allocation
This technical post breaks down congestion control mechanisms, focusing on the role of the transport…
AIDE : IDS for Linux Ubuntu Installation and Configuration
We present an IDS Installation and Configuration Tutorial on Linux Ubuntu. AIDE is also known…
Packet Tracer network with one router
In this tutorial, we will show you how to configure a network with just one…
How to Use Snap Behind a Proxy on Linux (Step-by-Step Guide)
In this guide, you’ll learn how to configure Snap to work behind a proxy, even…
How to Create a Network with a Switch in Packet Tracer – Step-by-Step Guide for Beginners
In this practical tutorial, I will show you how to create a simple switch network…
Why use Kali Linux inside VirtualBox?
In this article, we will see the main reasons for considering the use of Kali…