Today we will learn how to install pfBLocker NG in PFSense. pfBLocker is an excellent tool for restricting unwanted traffic and filtering content on your network.
pfBlocker NG is a powerful content blocker for pfSense that goes far beyond a simple ad blocker.
This tool allows you to implement blocklists of malicious IPs, filter unwanted web content, and utilize DNSBL (DNS-based Blackhole List) lists to prevent access to known dangerous domains.
This step-by-step guide will walk you through the process of installing and configuring pfBlocker NG on your pfSense, allowing you to take full advantage of the features of this incredible security package.
Get ready to strengthen your network protection with pfBlockerNG!
Installing the pfblockerng package in the pfsense
To install the pfblockerng package on the pfsense we will access the top menu of the pfsense and click “System“And then in”Package Manager
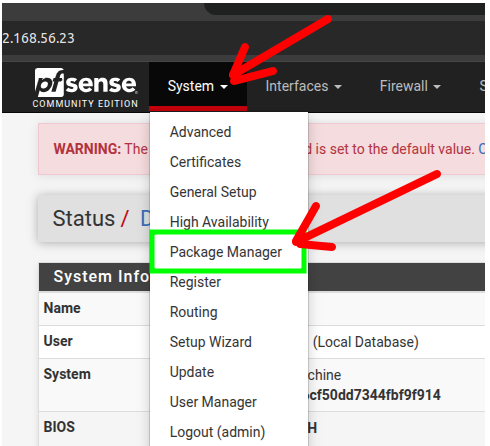
Then let’s click “AVAILABLE PACKAGES“and follow the instructions in the figure below.
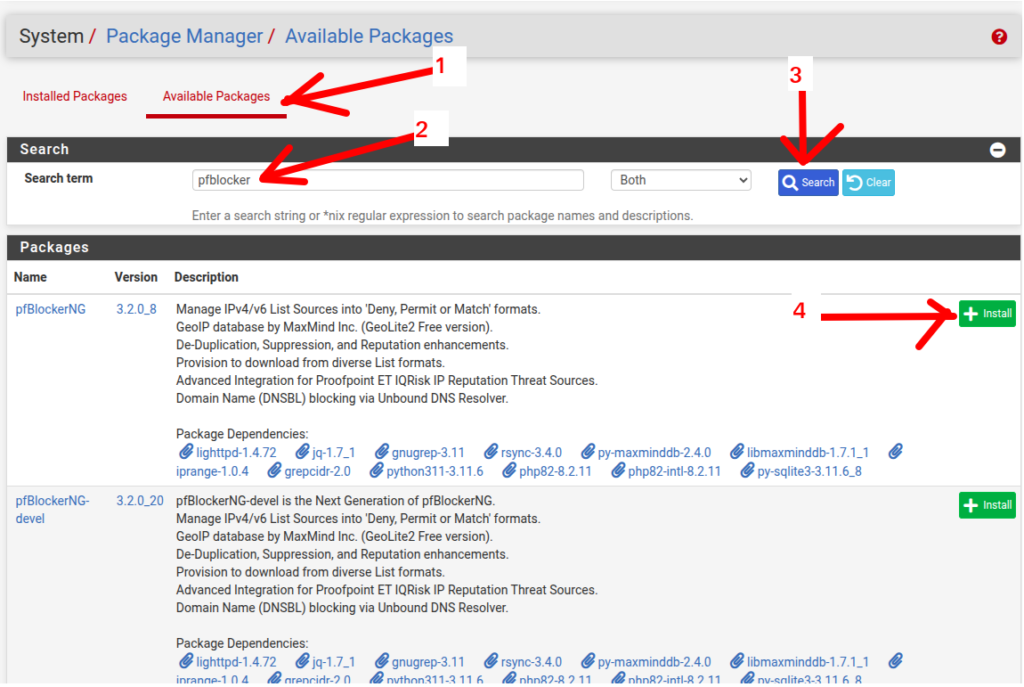
- AVAILABLE PACKAGES “ : Shows the packages we can install in the pfsense.
- Let’s insert the name of the package “pfblocker
- Let’s click “Search” to search for the package “pfblocker
- Let’s choose the first suggested package “pfblockerng “In this case, we don’t want to install the” PFBLOCKERNG-Devel “version.
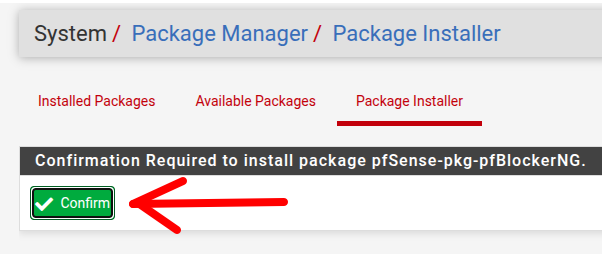
After that, a screen will appear asking if you confirm that you want to install the “pfblockerng“. Click Confirm.
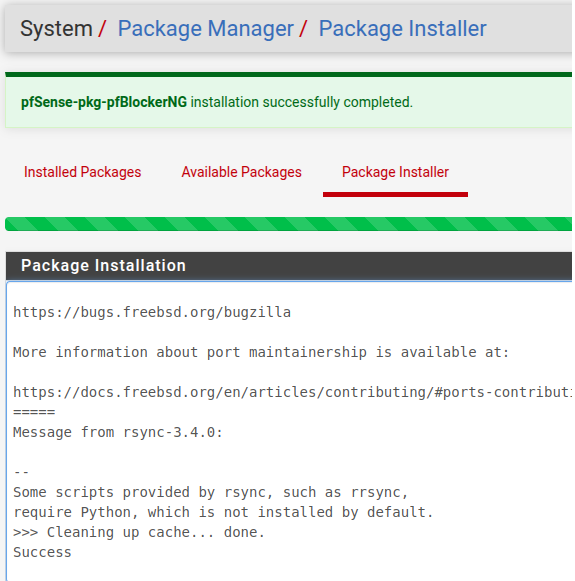
The installation will be started and at the end of the installation you will see a screen like the one in the figure below.
Configuring PFBLOCKERNG
After installing the pfblockerng, we will configure it by clicking on the top menu in “Firewall“And then in”pfblockerng
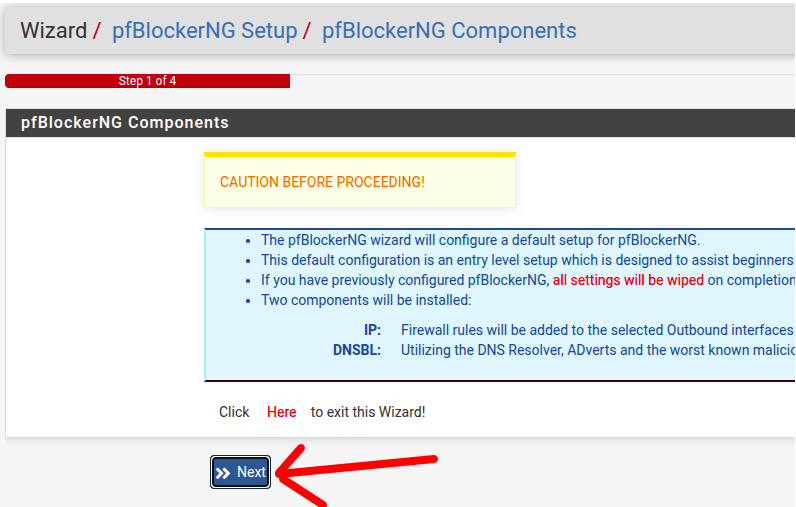
Then a setup screen will appear using a wizard configuration. I suggest you follow the configuration “wizard” if you have never installed the pfblocker.
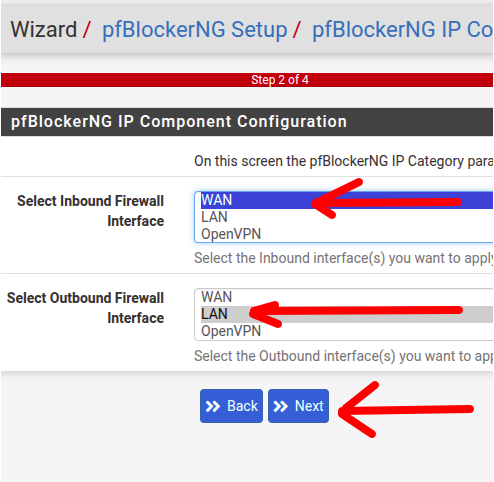
In the next screen, we will have the configuration of the interface that will be classified as “inbound” and the interface that will be classified as “outbound“.
- “Inbound “: deals with traffic that enters your system from an external network or the internet. In this case, the interface usually used is the WAN.
- Outbound “: It deals with traffic that leaves your system to an external network or to the internet. In this case, the interface usually used is the LAN.
After selecting the interfaces, let’s click “Next“.
Configuring DNSBL Webserver
Within “DNSBL Webserver Configuration“, we must be aware of some fields shown in the figure below and described shortly thereafter.
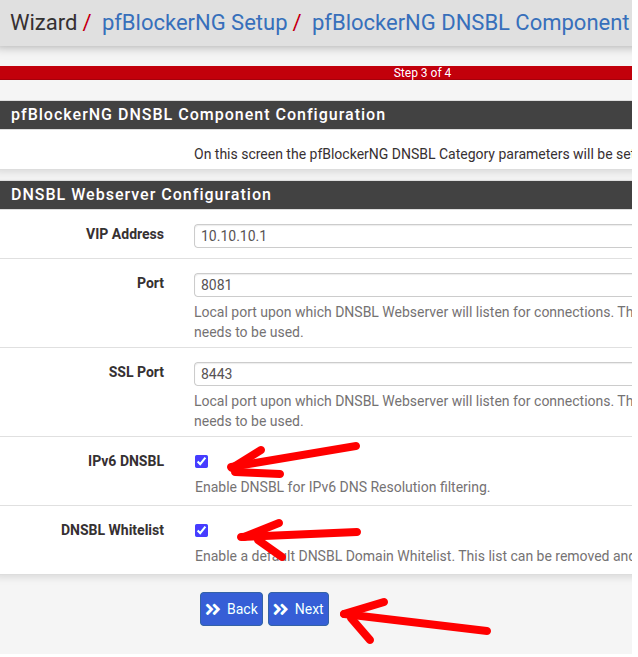
- “Virtual IP Address “: Here we are using the default IP “10.10.10.1 ” and this will be the IP that will be sent the rejected DNS requests. However, it is important to note that this IP ” 10.10.10.1 ” cannot exist in your network and if you already have this IP on your network you should choose another.
- “Porto” and “SSL PORT” : It will be the ports that the DNSBL server will listen and wait for connections.
- “IPv6 DNSBL” : Here, let’s score to use DNSBL with IPv6.
- “DNSBL WHITELIST” : Allows the use of the default “Whitelist ” and can be removed or changed later.
After that, we will see the configuration finishing screen and click “Finish“.
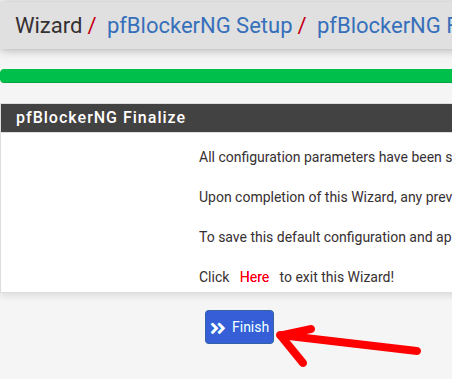
Pfblocker update after the initial configuration
Once we finish configuring, we will see a screen that starts a pfblocker update automatically. In this case, we will wait for the update to happen normally.
Testing the pfblocker
Now, let’s test the pfblocker using a machine that is in the PFSense LAN and that is configured to use the PFSense LAN IP as “gateway” and as a DNS server.
The scenario we are using can be represented by the figure below.

In the client machine, which in our scenario has the IP “192.168.56.88“, let’s set up the network interface to receive static IP and we will use the settings presented in the figure below and described shortly thereafter.
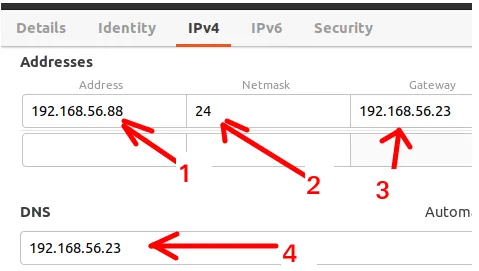
- 1: The client machine IP.
- 2: The mask used on the network that is the interface PFSENSE LAN.
- 3: PFSENSE LAN INTERFACE IP to be used as gateway.
- 4: PFSense’s LAN Interface IP to be used as DNS server.
After setting up the client machine to point to the PFSense that is running the PFBLOCKER, let’s surf the internet using the client machine.
Ideally, you use the client machine to navigate advertisements.
After navigating websites with the client machine, return to the PFSense web interface and go to “Firewall” and then “pfblockerng“. Within “pfblockerng“, go to the tab menu “REPORTS” and then “Alerts“. Then you will see the alerts generated as in the figure below.
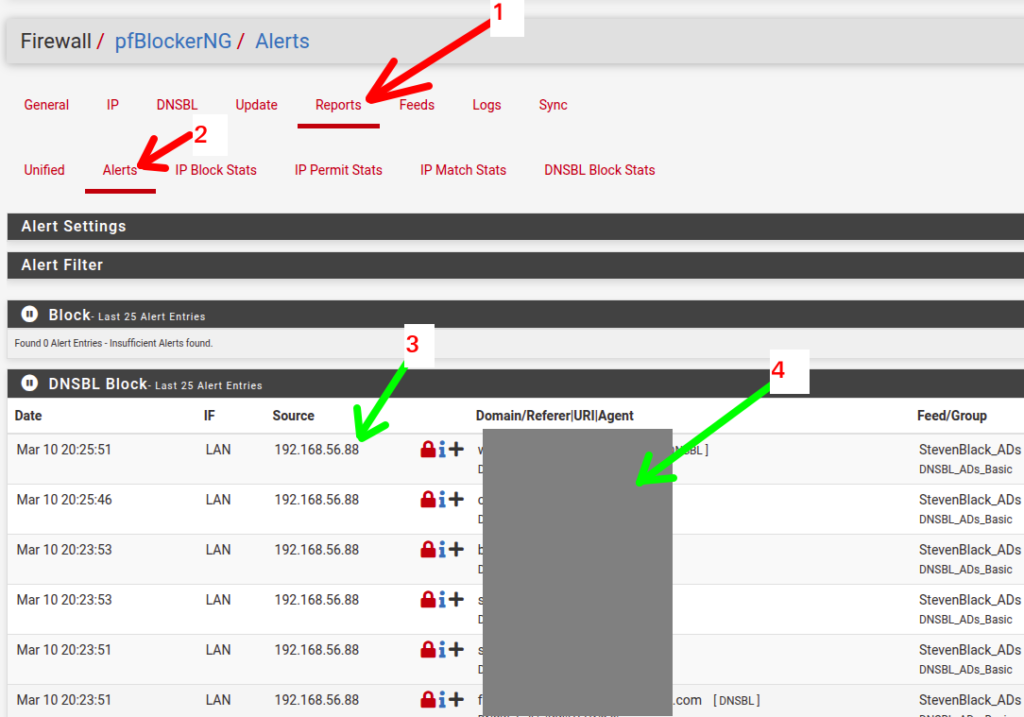
And finally we ended the PFBLOCKER NG installation in the PFSense. Remembering that this is just the installation and a basic configuration. See the other posts to find out more PFBLockerng settings.
Veja mais:
pfBlockerNG Customize Blocklist
PfBlockerNG: Exception List for Clients
https://docs.netgate.com/pfsense/en/latest/packages/pfblocker.html

Juliana Mascarenhas
Data Scientist and Master in Computer Modeling by LNCC.
Computer Engineer

