Due to the scarcity of IPV4 addresses, a solution that started to gain strength was using NAT (Network Address Translation).
Thus, NAT allows machines from within a network to communicate with another network as if they were leaving the network with the same IP.
Consequently, if we are on a private network with 50 computers, we could only have one public IP. The NAT solution is quite advantageous because there is a shortage of IPV4 public IPs.
Internet communications use the public IP, while on the private network, we may use IPs reserved for private use.
It is noteworthy that private IPs do not work on the internet. This behavior occurs because routers are programmed to discard IPs in the private IP category.
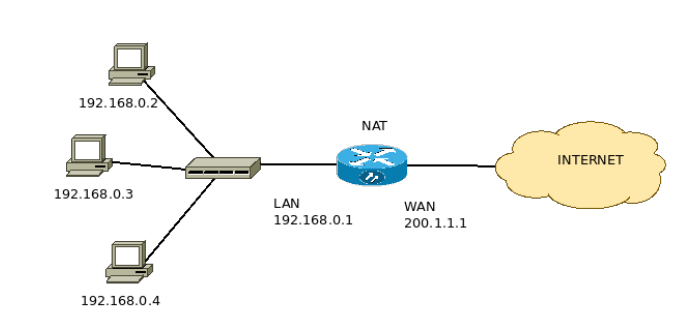
Figure 1 shows a network where the router’s LAN interface is on the private network, and the WAN interface is on the public Internet network.
Thus, the network administrator only needs a public IP for this scenario. This configuration is because the other three internal machines use private IPs.
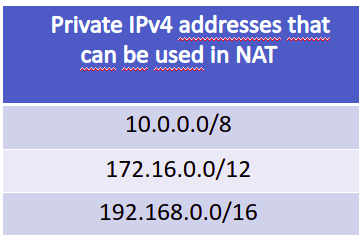
Figure 2 presents a block of private IPs that can be freely used within internal networks. In this way, the network administrator can use different netmasks with these blocks of IPs to give addresses to their devices.
In addition to the two blocks shown in Figure 2, there is block 169.254.0.0/16. However, this last block is not used for NAT.
Types of NAT
Static NAT : Maps between a private IP and a public IP. Thus, it uses a one-to-one mapping.
Dynamic NAT: maps private addresses to a set of public addresses.
PAT Port Address Translation: Maps between addresses private and public using the transport layer ports.
• (very used)
• This will be the NAT covered in this class
How does NAT work?
NAT will use a table with IP addresses and Ports to forward traffic between hosts on the internal network and hosts on the external network.
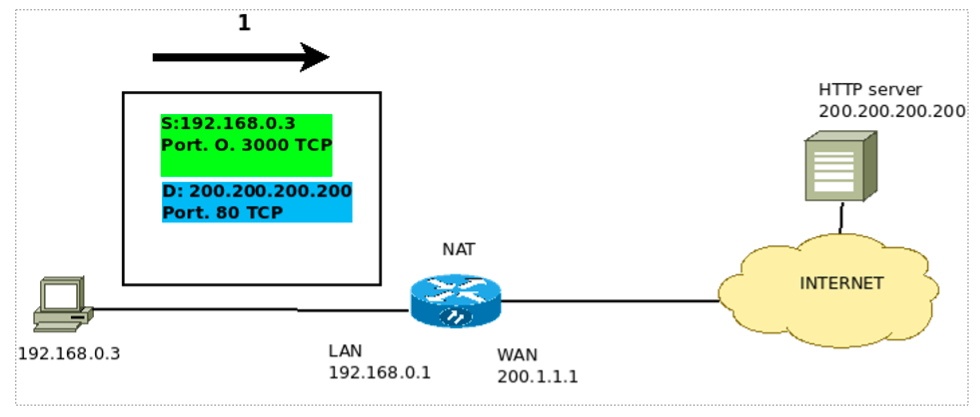
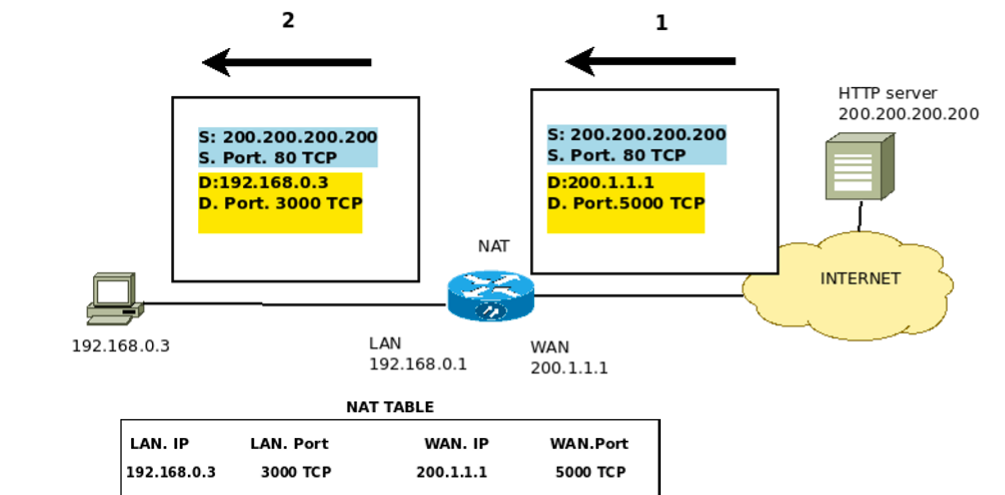
In Figure 3, we can see the first packet leaving IP 192.168.0.3 going towards the HTTP server.
This way, we can verify that the packet leaves with source IP address = 192.168.0.3 and with source port = 3000 TCP. Consequently, it is worth mentioning that this port was chosen randomly.
Thus, in the client-server model of TCP/IP, clients often use random ports to communicate with server ports. On the other hand, server ports should be well-known. The reason is that the client needs to know which port to connect to.
So, we can see that the destination IP used in the IP packet will be the IP of the HTTP Server server, and the destination port = 80.
This way, the client already knows that it is accessing a server and that this server listens on TCP port 80.
Additionally, we know that port 80 TCP is used to provide the service of delivering HTTP pages. Therefore, port 80 TCP is used by the HTTP protocol.
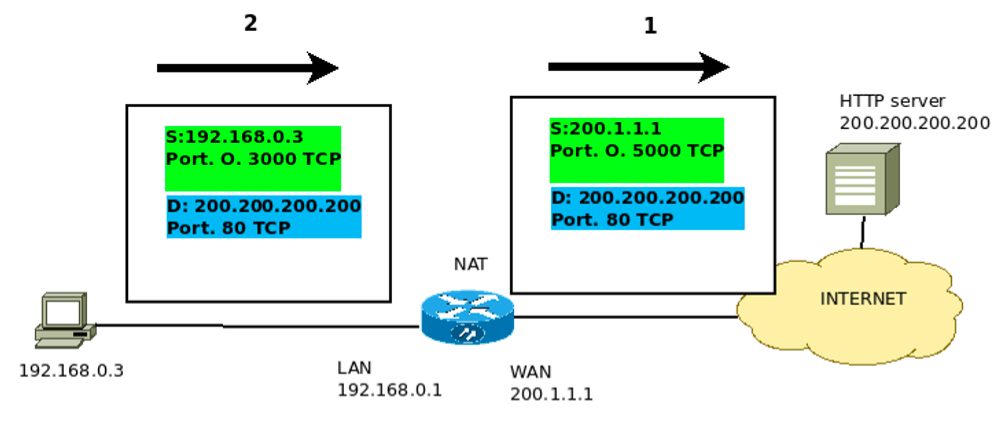
We can see that package one has already gone through NAT, Figure 4. In this way, we are presenting NAT in the PAT model. We use transport layer ports to translate between machines on the internal network and public IPs.
We can see that the source of the package is modified. That is because NAT needs to change the source IP. After all, the private IP 192.168.0.3 cannot exist on the internet. So in this, the IP is changed to the public IP of the rotator that performs the NAT.
Additionally, NAT also changes the source port. People often ask themselves: why can’t you use the same port?
The answer to this question is simple: NAT cannot prevent two or more hosts from using the same port to communicate with a public network IP. In this way, NAT changes the source port to an available port in its set of ports.
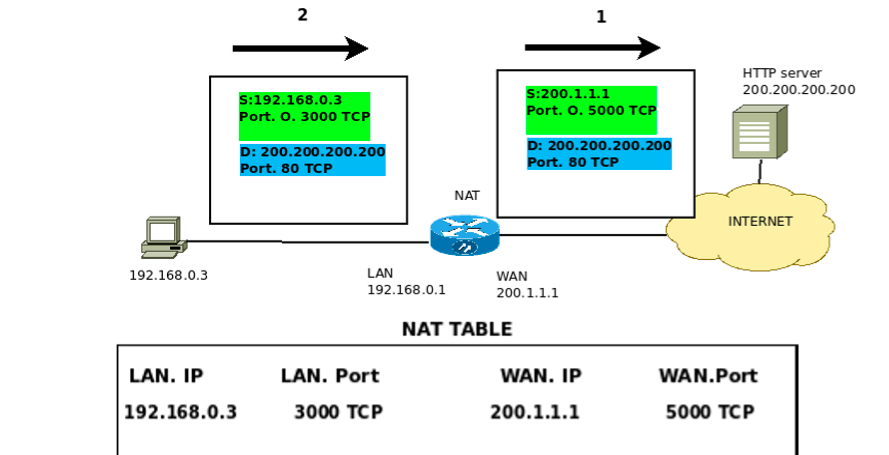
When a machine on the internal network communicates with other public IPs, the NAT must create a table.
This table is used so that NAT maintains the communication state between the internal host and the host with a public IP. Also, the NAT table is essential to ensure it can return when there is a communication response.
Consequently, the router table that makes the NAT can redirect the response traffic to the host that initiated the communication.
Is NAT more secure?
NAT provides additional security for machines that are inside the private network. That is because devices with a private IP cannot be seen directly by hosts on the Internet.
In this way, NAT prevents access to machines with private IPs unless the private device initiates communication or uses port-forwarding.
So when a machine with private IP starts to communicate with a device with public IP, the IP of the private machine will be translated to the public IP of the NAT router.
However, machines are still vulnerable to attacks that cause internal devices to initiate communication, such as the reverse shell.
Does NAT violate the layer rule?
Some authors argue that NAT violates the layer rule. That is because NAT causes a router to change the transport layer by changing the source port.
However, despite this issue of breaking the rules, NAT has been a handy tool over the years.
How does packet response work in NAT?
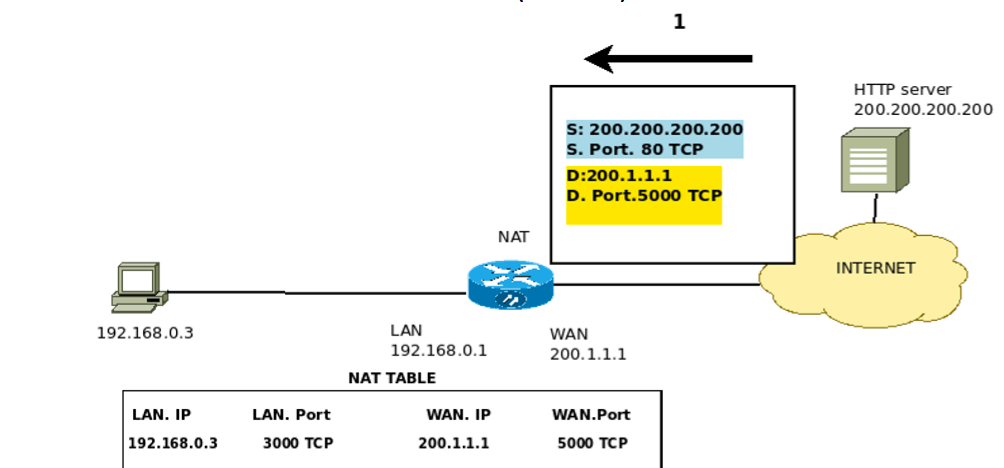
The communications response between the private network and the public IPs occurs using the NAT table, Figure 6 and Figure 7.
This way, when a reply arrives at the router’s public IP, it will check which port is the destination and if this port is in your NAT table.
So, if the destination port is mapped in its NAT table, the NAT table will be used to know where the packet should be forwarded. Thus, the NAT table is essential for the return of communications to occur correctly.
NAT with 2 PCs on LAN network
Now let’s add a second machine, 192.168.0.2, and start communication with the same WEB server.
This way, we will demonstrate how NAT handles two internal clients communicating with public IPs.
Initially, in Figure 8, computer 192.168.0.2 starts its communication and chooses a random port. In this case, the selected port was 9000 TCP.
So the source address is now 192.168.0.2, and the source port is 9000 TCP. However, destination addresses remain the same as in the previous communication. In other words, destination IP = public IP of the WEB server, and destination port = 80 TCP.
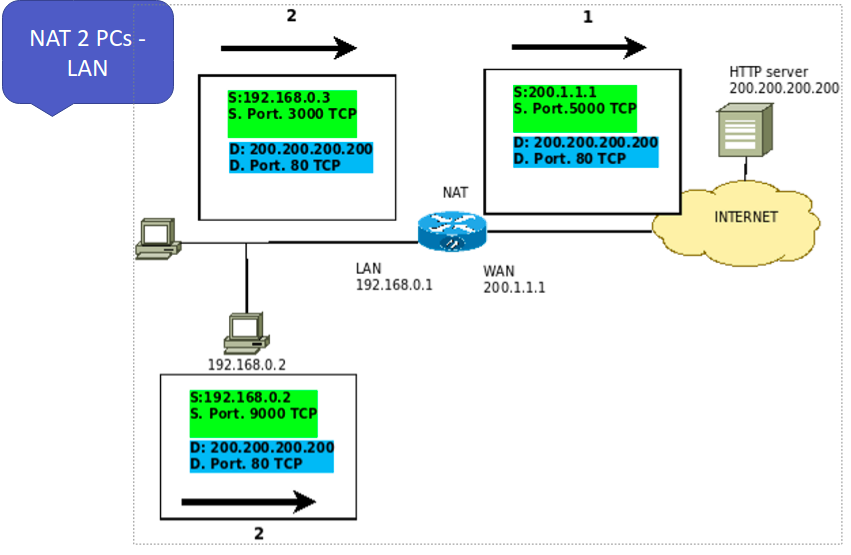
After going through the NAT, Figure 9, the package originating on the 192.168.0.2 computer is modified. In this modification, the source IP and source port are changed.
Thus, after the NAT, we have the packet with the source addresses IP = public IP of the NAT router and port 4400 TCP. However, the destination IP and destination port remain the same. That is, destination IP = WEB server IP and destination port = 80 TCP.
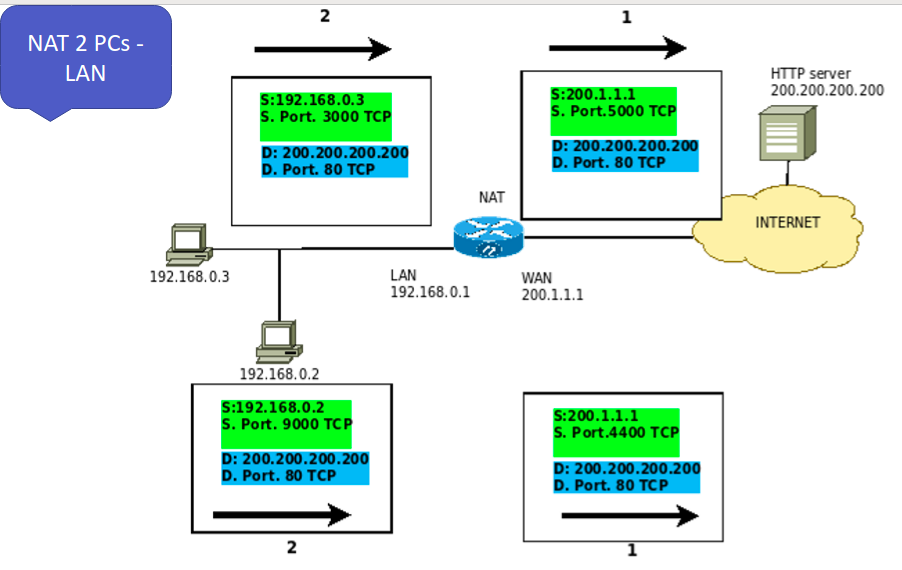
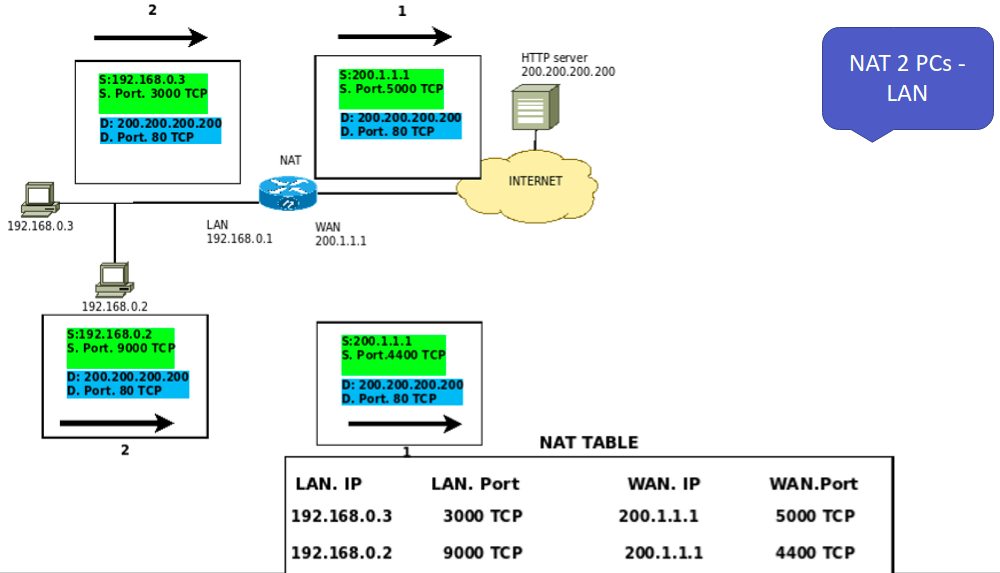
Finally, let’s look at the NAT table. So, after the computers’ communication starts with IPs 192.168.0.3 and 192.168.0.2, we have the NAT table formed in the router doing the NAT.
In this way, NAT can distinguish the different flows of internal machines and their external communications using the IPs and ports in the NAT table.
Port Forwarding on NAT
Now let’s talk about Port Forwarding. Port forwarding is extremely important when we want to share a service behind a NAT.
Thus, we can use port forwarding to have a WEB server on an internal network to be exposed on the internet.
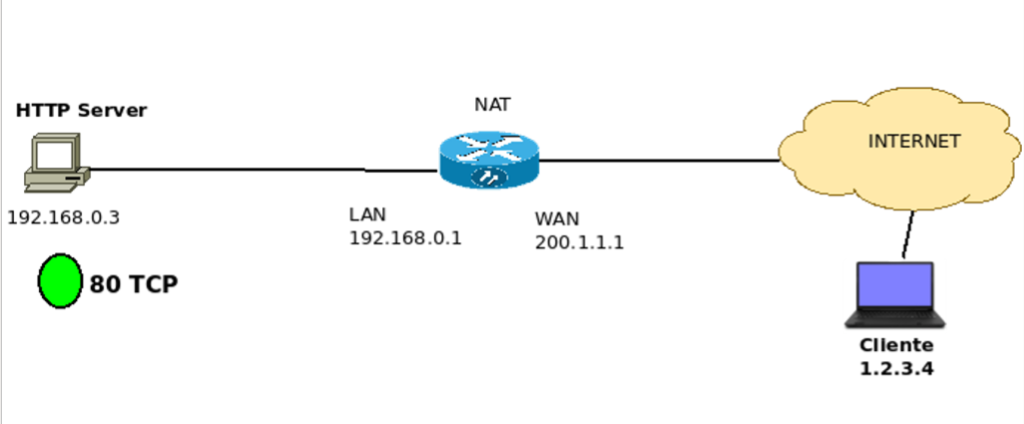
In this example, let’s assume that the computer represented by IP 192.168.0.3 wants to expose its WEB server, Figure 11.
We know that a WEB HTTP server will default listen on TCP port 80. So we need to create a rule in NAT to allow access originating from public IPs to access the machine 192.168.0.3 on port 80 TCP.
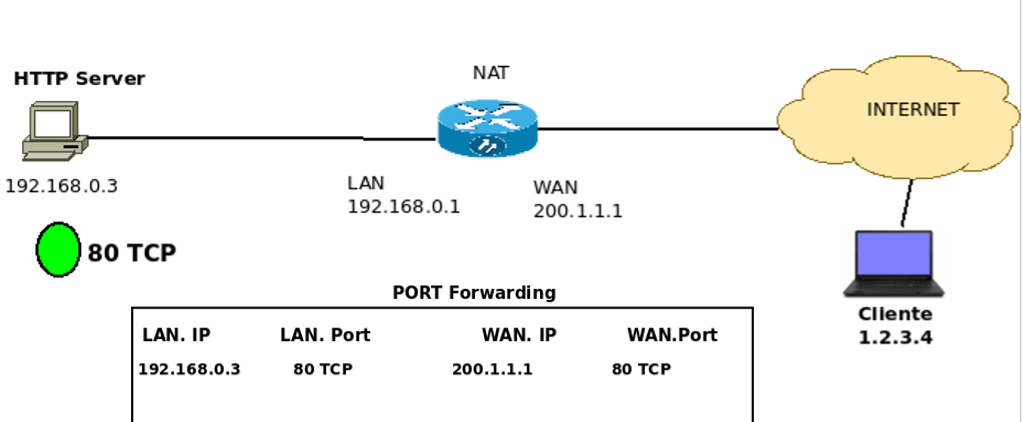
To do this, let’s create a port forwarding in the NAT router table, Figure 12. So let’s create a rule that indicates that everything arriving at the NAT router’s public IP interface on TCP port 80 will be routed to IP 192.168.0.3 in port 80 TCP.
Thus, we allow connections from public IPs to communicate directly with the public IP of the NAT router. Consequently, we allow access to the HTTP server of host 192.168.0.3 to be accessed externally.
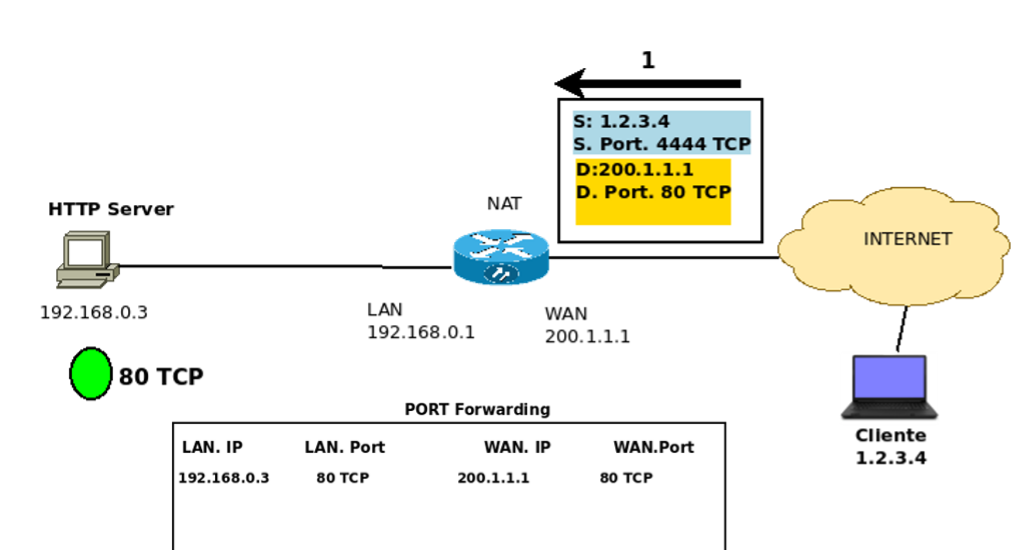
However, it is worth remembering that the external machines only communicate with the public IP of the NAT router. Thus, when a fictitious IP 1.2.3.4 initiates communication with the WEB server, it must indicate the public IP of the NAT router and the port mapped to port forwarding =80 TCP as the packet’s destination.
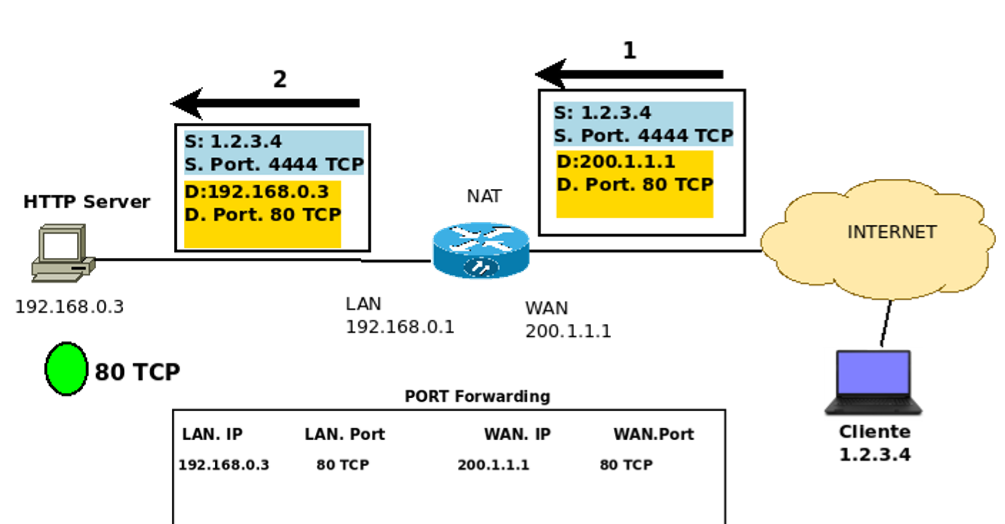
After the packet passes through the forwarding port, the destination addresses are changed to allow the redirection of the packet to the WEB server within the internal network, Figure 14.
Thus, the destination IP is changed to 192.168.0.3, and the port continues to the same 80 TCP. However, although the port remains the same, using a different internal port than the externally mapped port in port forwarding would be perfectly possible.
We have an solved exercise using NAT: https://youtu.be/azpBws4QPOc
Read more
HTTP Protocol – How Does It Work?

Juliana Mascarenhas
Data Scientist and Master in Computer Modeling by LNCC.
Computer Engineer
Packet Tracer network with one router
In this tutorial, we will show you how to configure a network with just one…
How to Use Snap Behind a Proxy on Linux (Step-by-Step Guide)
In this guide, you’ll learn how to configure Snap to work behind a proxy, even…
How to Create a Network with a Switch in Packet Tracer – Step-by-Step Guide for Beginners
In this practical tutorial, I will show you how to create a simple switch network…
Why use Kali Linux inside VirtualBox?
In this article, we will see the main reasons for considering the use of Kali…
How to install pfBlocker on pfSense: step by step guide
Today we will learn how to install pfBLocker NG in PFSense. pfBLocker is an excellent…
Packet Tracer for Dummies: Setting Up Your First Network with 2 PCs (Quick Start Guide)
Are you ready to take the first step into the fascinating world of computer networks?…