In this article we will talk about HTTP cookies, a set of data that allows the server/website to provide targeted services to its users, tracking and identifying its customers. To know how the HTTP protocol works, read the article: HTTP – WEB communication protocol.
Cookies HTTP
As already mentioned, the HTTP protocol is stateless. This way, the connection state is not stored. However, there will be times when it will be helpful, or even need to identify your customers in some way. In this scenario comes the concept of cookies.
The growing use of web stores and web applications brings the need to keep customer persistent data. So what is the role of cookies in this scenario? They provide the ability to track, identify and/or provide customer functions.
Defined by RFC 6265, as the information contained in cookies varies according to the user’s browsing history. However, the feature of cookies are used to save user information as an advantage of in the monitoring of users.
Communication with cookies
When connecting to a website that uses http cookies, a cookie header line is sent in the server’s http response. With this header, the client stores his cookie. Whenever there is a related page access, the client will send the stored value of the cookie corresponding to the page.
In order for a connection to be able to maintain persistent data, a structure is needed. Thus, we have three components that make up cookies: cookie header line, cookie file, and cookie’s information on the back-end.
Cookie header line is present in HTTP messages: request and response. These fields an exchange of messages will identify the customer for the server. If it is the first time that the user connects, he will receive an identification and the client file will be used.
Consequently, this client file is known as a cookie file. This file is kept on the client but managed by the browser. The cookie file is stored as information about the customer. This information is client identification related to the websites, information to keep the user logged in the website and other information about it.
This information can also be used to access the user. We’ll talk in the next topic about a possible information theft scenario.
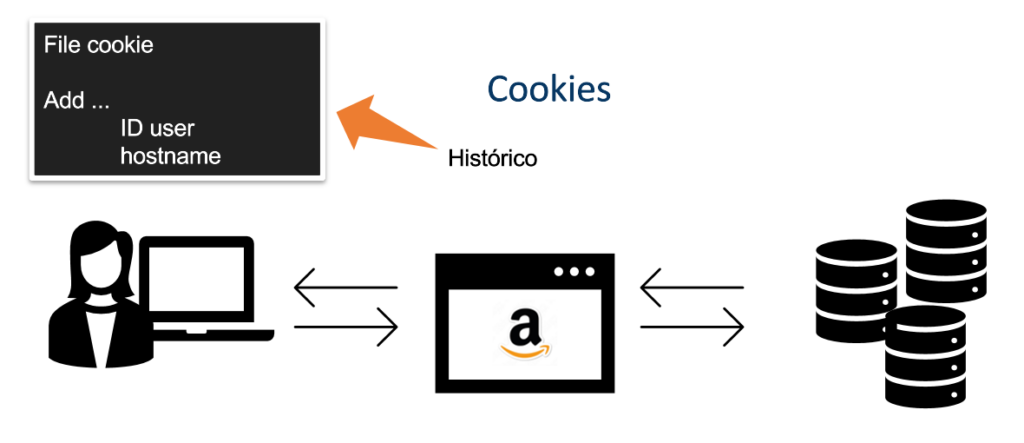
Of course, this information must be stored on both the client and the server. Therefore, in addition to the cookie file, the server has the back-end database on the website. In this database, it must have identification and other information related to your customers.
Cookie and Privacy
The cookie can be considered a violation of privacy, because through cookies companies or people can trace a user’s browsing profile. For this reason, the LGPD has brought stricter guidelines for companies that handle their users’ data. Currently, the website must inform customers about the use of cookies. In addition, you must request your consent to use the data. However, this consent is not required.
There is still an illegitimate use of this data. Hackers may also use cookies to obtain private information from their victims. How can this happen?
Imagine that you keep your websites logged on your machine. This makes life easier, as we don’t need to log in and enter the password all the time. But think about it… this information is stored in the cookies file. The file contains information relating the user’s session on the the website.
Ok, but how can hacker use my cookie files? Continuing our example, imagine that there is a security falt in your machine and a malicious user gains access to your data. In possession of your cookie file, the malicious agent can log into websites using legitimate user information. Avoid leaving account logged in, prevent storing session management information.
How does sending cookies over an HTTP connection work?
An HTTP request message is sent when a user initiates an HTTP connection. Upon receiving the request message, there will be a check on the server’s database. Consequently, if it is the user’s first access to the site, there will not be an ID associated with that user. Thus, an update with an insert into the database will take place. Afterwards, the server will send a message response setting the user ID by the cookie header line. This user ID, along with other information, will be inserted into the cookie file that is managed by the client’s browser.
We see the example of the process by animation in the video below.
To learn more about the topic
Bibliographic references
- Cookies HTTP by Mozilla developer
- Kurose, James F., and Keith W. Ross. “Computer Networks and the Internet.” Pearson – 6° edition
- Tanenbaum, Andrew et al. “Computer Networks” Pearson – 5° edition.
- RFC 6265 – HTTP Managment State Mechanism
Simplificando Redes on the social media


